西湖论剑2021WP-👴🚪的第二次出征
爷们的自留地
事情的起因很简单:
起初是👴🚪想和各位👴线下面基,想看看哪个比赛容易进线下;
然后在风和🌞丽的某一天,群里突然出现了西湖论⚔️的邀请函;
至此,👴🚪面基的想法就变成了,去西湖击剑。
👴🚪拼了命的上分,然后静止在了43名,差十三名才能进线下。
明年再来吧,还有 HWS 的冬令营能面基,并不是对击剑的执著,而是对 ctf 的热爱。
做出了一半的题目,这里把👴🚪写的wp放上来,记录一下。
(不要问👴明明是个pwn✋为什么打了一天MISC,问就是太菜了)
MISC
签到 By-Da1Da1A0E
YUSA的小秘密 By-Shangu
首先,从提示就能想到这道题大概的考察点,LSB加上不止RGB,说明采用的不是RGB,参考Bytectf2020的第一道图片题:https://bytectf.feishu.cn/docs/doccnqzpGCWH1hkDf5ljGdjOJYg#qHRUCR
那道题的思路是,转换 YCrCb 通道,再提取出 三色道,分别是三张二维码片段,最后手动拼接一下或者合成都可以。
参考那道题的思路,首先对Yusa照片色彩空间转换:
1 | PYTHON |
然后二值化处理:
1 | PYTHON |
这里有个坑,让我浪费了好长时间,我的 python 的 imshow 只能显示图片的一部分。
然而这道题比去年的还简单,二值化以后直接能看到flag。
尽量不要用 imshow 用 imwirte,得到blue的图像中得到flag:
1 | PYTHON |
Yusa的秘密 By-Shangu
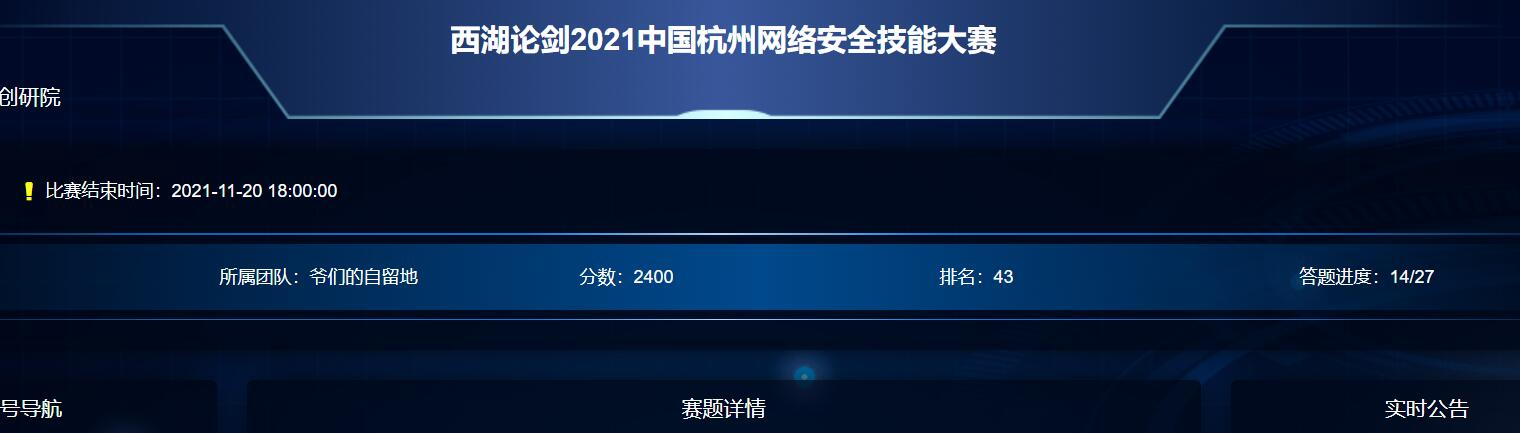
内存题,先用 passwordkit 嗦一下看看有没有密码,得到密码 YusaYusa520,刚好是Who_Am_I 的解压密码:
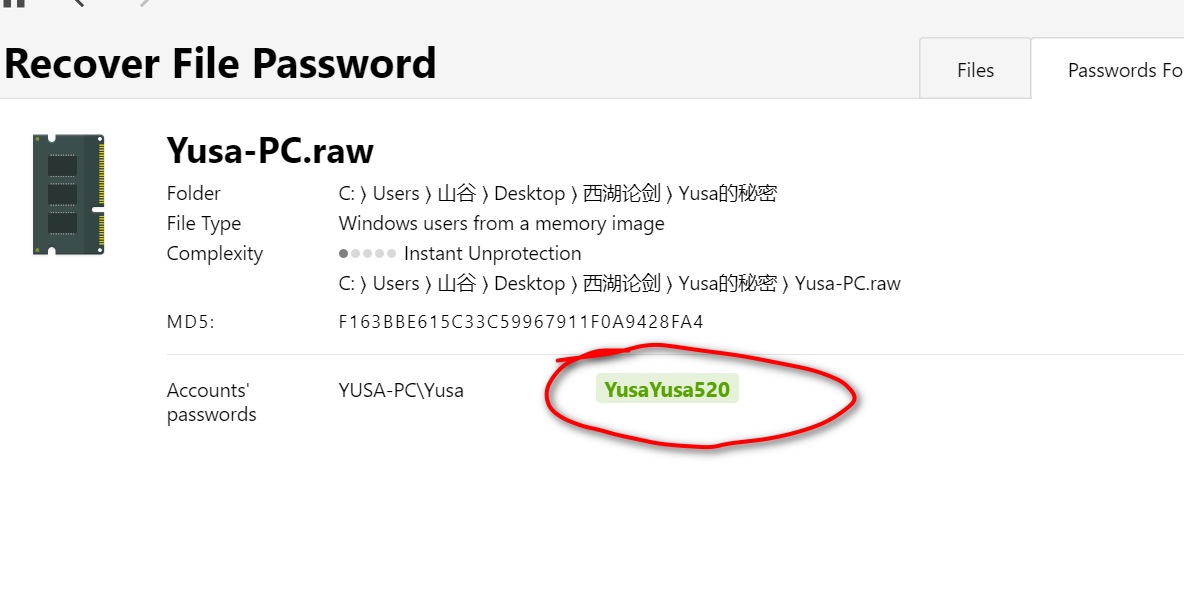
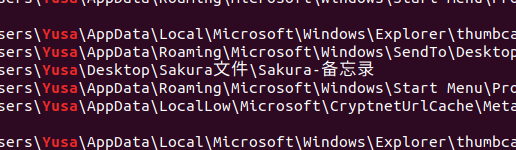
上取证大师,全局搜索一下提示里出现的俩关键词 “Yusa” 和 “Sakura” ,得到下面的这些文件:
在查文件过程中,顺手发现了几个中文的文件,之后都会用到,提取 dump 出来。
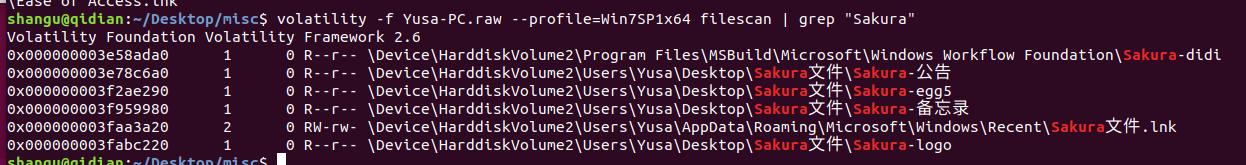
0x000000003f959980 1 0 R–r-- \Device\HarddiskVolume2\Users\Yusa\Desktop\Sakura文件\Sakura-备忘录
0x000000003e748f20 1 0 R–r-d \Device\HarddiskVolume2\Users\Yusa\Contacts\Yusa.contact
0x000000003e78c6a0 1 0 R–r-- \Device\HarddiskVolume2\Users\Yusa\Desktop\Sakura文件\Sakura-公告
0x000000003e20d900 1 0 R–r-- \Device\HarddiskVolume2\Users\Yusa\Desktop\新建文本文档.txt
具体哪个是哪个我也忘了,dump出来文件名会变,有用的文件如下:
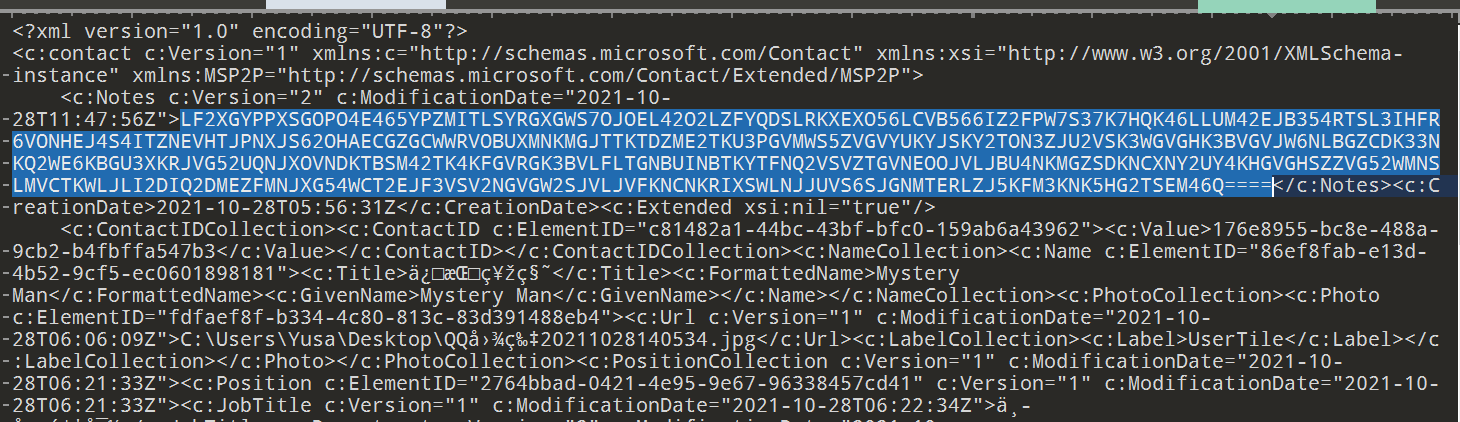
根据公告里的提示,去查找 .contact 联系人文件,一共找到 Yusa.contact 和Man.contact 两个文件
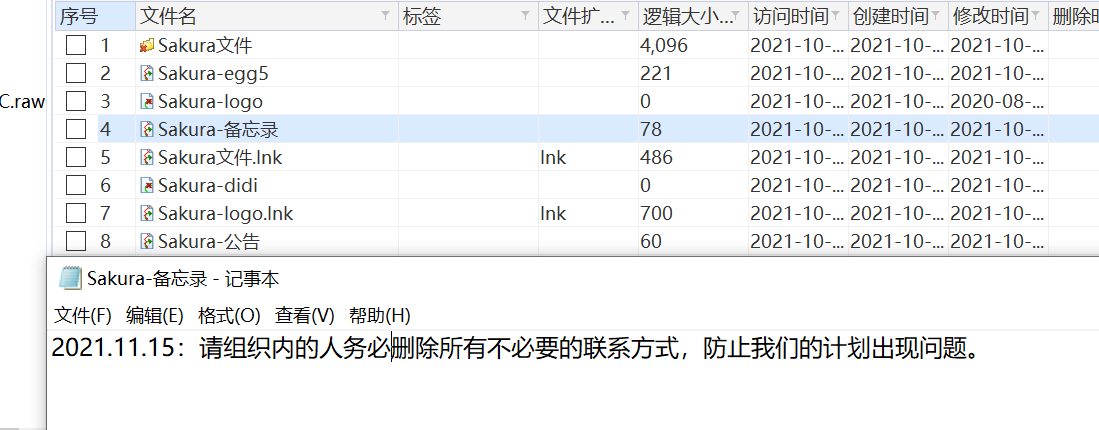
两个联系人文件中有彩蛋一个,还有个base加密,cyberchef一把嗦出来得到 一个解压密码:
这是你会用到的key,可以用它打开组织给你的工具。工具命名依照了传统规则。key:820ac92b9f58142bbbc27ca295f1cf48
然后按照传统,找一下压缩包文件,都导出来挨个试密码,最后确定这个密码打开了 Sakura-didi 这个文件,里面存着 bmp 文件。还有一个放着 exp 的压缩包没有找到密码。
回头用取证大师在看一下进程有没有可疑的信息,发现了老熟人,windows便签:
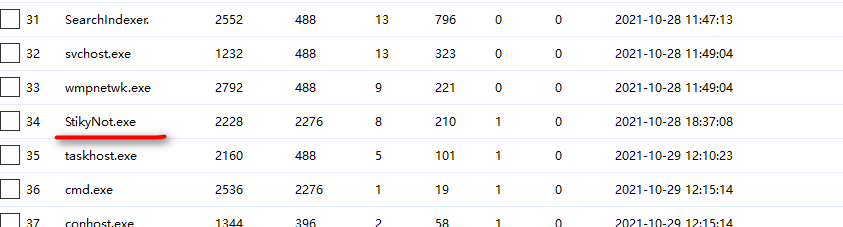
win7的便签后缀名是snt,搜索一下得到最后一个解压密码:
发现取证大师恢复不了,用 vol dump出来,这里需要替换掉本地的便签文件,不知道是不是我win10坏了,下了个win7虚拟机,用win7可以开:
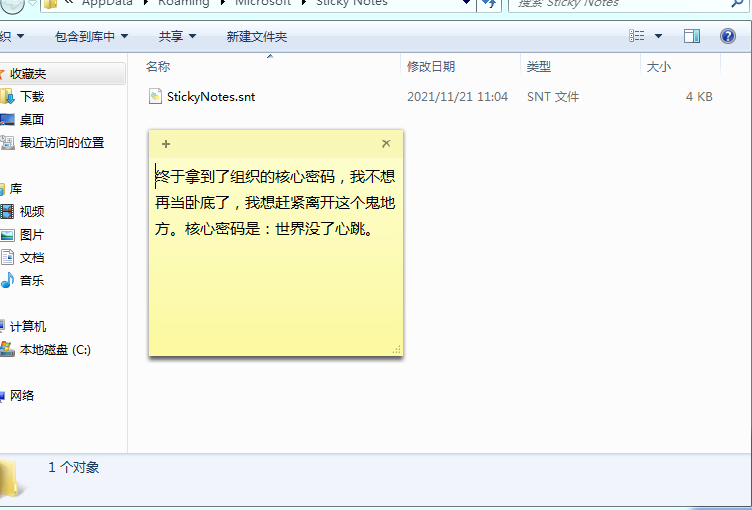
解压三个文件的到的:
Who_Am_I exp.py key.bmp
分析exp里的加密流程以后,发现直接改一下flag 和 who的位置,然后改成可写,就可以得到flag:
1 | PYTHON |
用stegsolve处理图片,找到flag,就是有点废眼睛:
flag在图的下面。
Crypto
hardrsa By-Shangu
原题:https://blog.csdn.net/a5555678744/article/details/117717969
照搬一下代码:
1 | PYTHON |
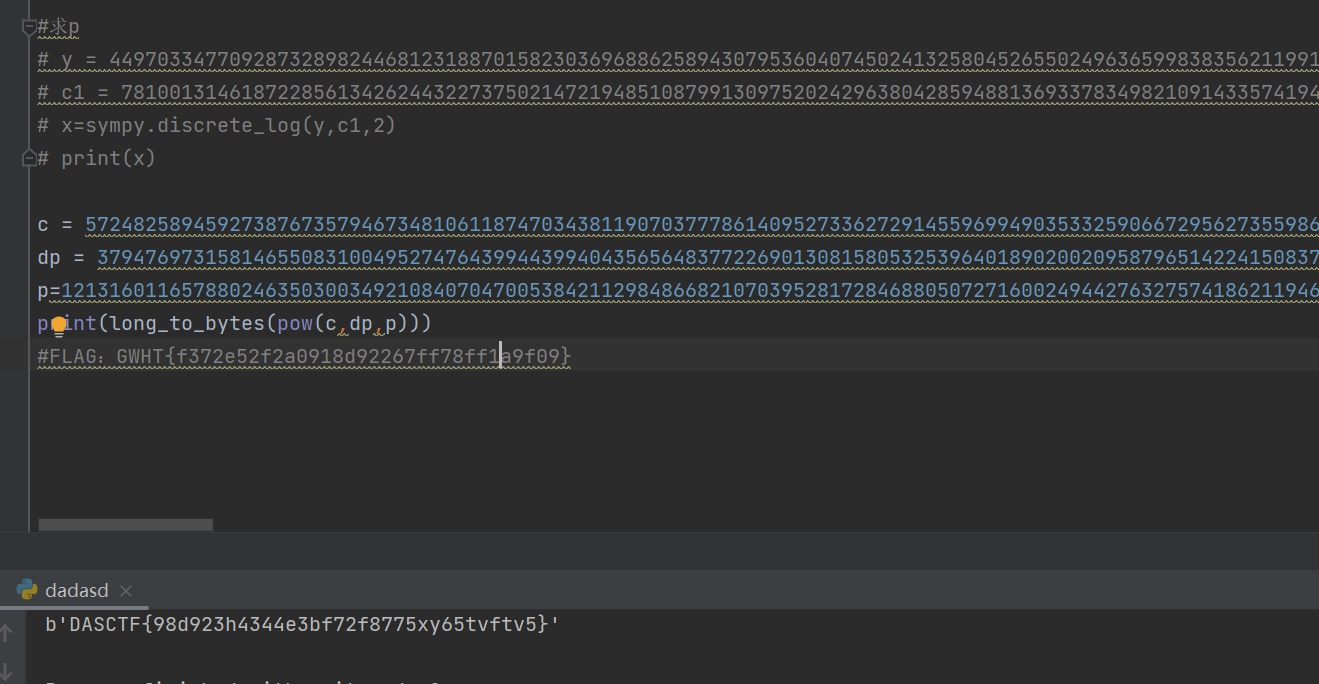
求 p 脚本运算量很大,放在服务器跑了四分钟才出来,就不再跑了。
之后照抄脚本,在sage跑一下得到p:
1 | PYTHON |
最后执行脚本得到flag:
unknown_dsa By-Tr0jAn
解佩尔方程得ul和vl,都是佩尔方程的最小解,解完之后可以通过excrt拿到m1 m2,然后就可以解出p,q
$$
pq与(p-1)/q
然后由计算得到,最后求与得到然后由计算得到k,最后求x1与x2得到flag
\s1 \equiv (hm1+x1r1) * k^{-1}(mod \ q)
\s2 \equiv (hm2+x1*r1) * k^{-1}(mod \ q)
$$
之后直接求x1与x2即可。
exp:
1 | PYTHON |
Get flag!
DASCTF{f11bad18f529750fe52c56eed85d001b}
Crypto5-密码人集合 By-0xK4ws
nc连上去发现是做数独题 9x9的数独
网上找一个脚本跑一下就完事
1 | PYTHON |
https://www.pythonheidong.com/blog/article/611784/69977d3f01fb34121944/
然后再进行数字和字符之间的替换就行
西湖论剑我要拿第一
1 2 3 4 5 6 7 8 9
西湖论剑我要拿第一
以上是对应关系
然后输入解拿到flag
WEB
EZupload By-0kam1 & Da1Da1A0E
首先view-source 看到 ?source=1
拿到源码
然后在本地写一个文件上传到远程的html
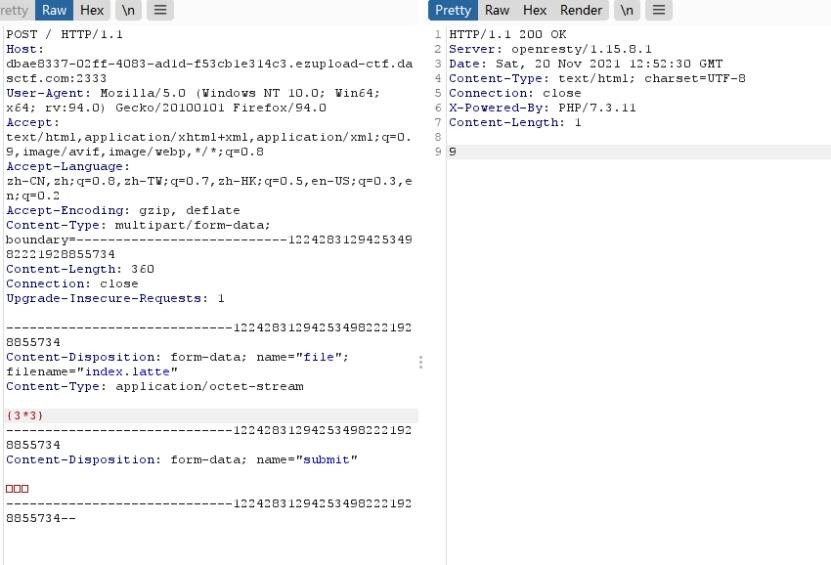
然后我们就开始了文件上传之路
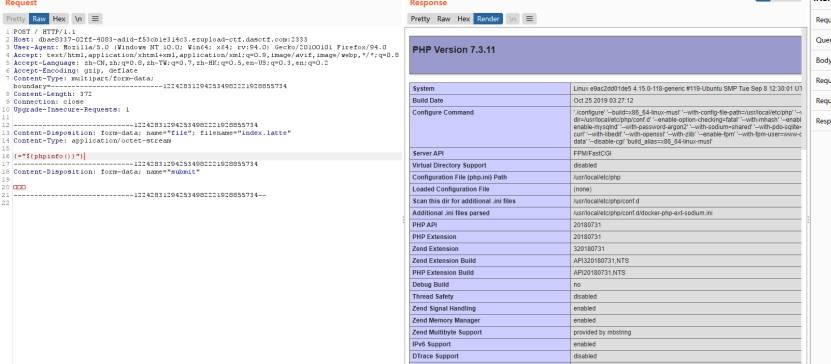
我们上传一个index.latte 发现能被渲染。
然后试着代码执行,用phpinfo实现
因为echo “${phpinfo()}”;
=等同于echo
双引号内的变量不会被当成字符串,所以组成
{=“${phpinfo()}”}
等同于 echo “${PHPINFO()}”
即打出payload
因为``可以进行代码执行,但是不会回显,所以我们选择用>将结果写入txt文件读取
故payload为
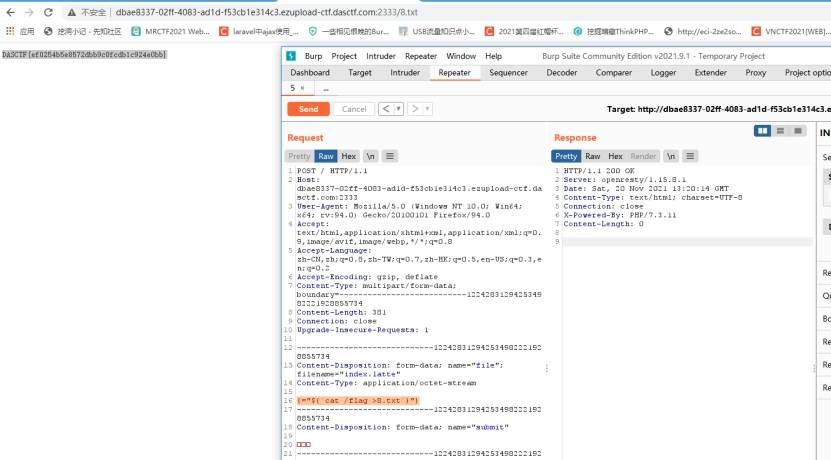
{=“${cat /flag >8.txt}”}
拿到flag
灏妹的web By-Da1Da1A0E & 0kam1
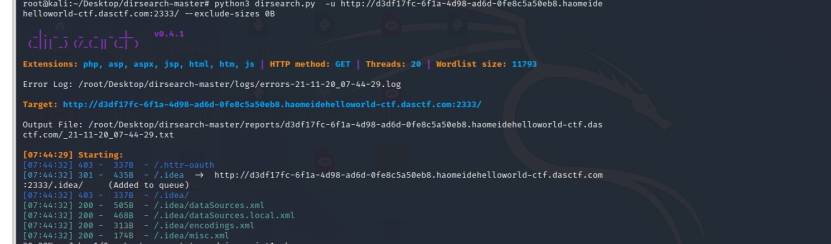
首先进入题目,看到一张图片,啥都没有。。头文件也没啥东西,忙碌了半天的呆师傅决定直接dirsearch
python3 dirsearch.py -u http://d3df17fc-6f1a-4d98-ad6d-0fe8c5a50eb8.haomeidehelloworld-ctf.dasctf.com:2333/ --exclude-sizes 0B
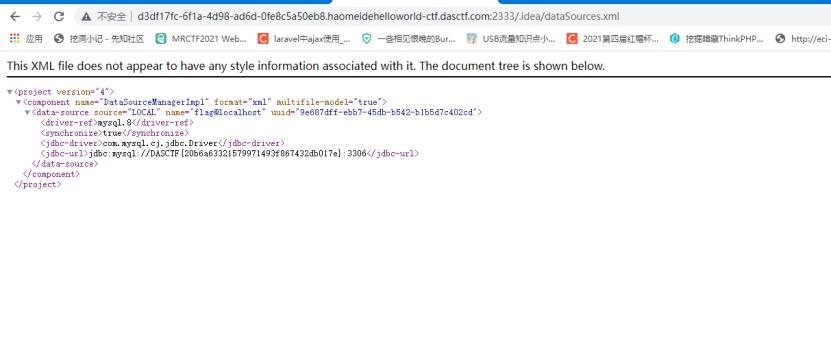
扫描,发现idea泄露。、
逐个看过去。
访问第一个页面就找到了flag
EasyTp By-0kam1
打开网站是这个
http://8ee57807-23ba-44f3-86c0-28266918cb75.easytp-ctf.dasctf.com:2333/
再看了下题目说是public文件下
http://8ee57807-23ba-44f3-86c0-28266918cb75.easytp-ctf.dasctf.com:2333/public/
提示缺参数
构造
是个这玩意扔bp里面去fuzz
常用的php文件
得到三个
Index.php System.php PEAR.php
因为题目提示说是easytp
那就想办法tp爆错爆出版本呗
根据tp路由+Index文件内容的思路去构造爆错语句
public/index.php/unser
确定tp框架版本
查相关的漏洞点
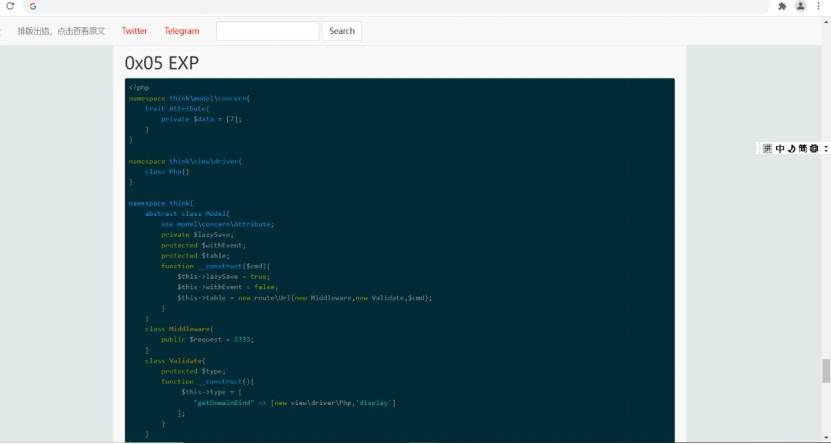
尝试了几个链
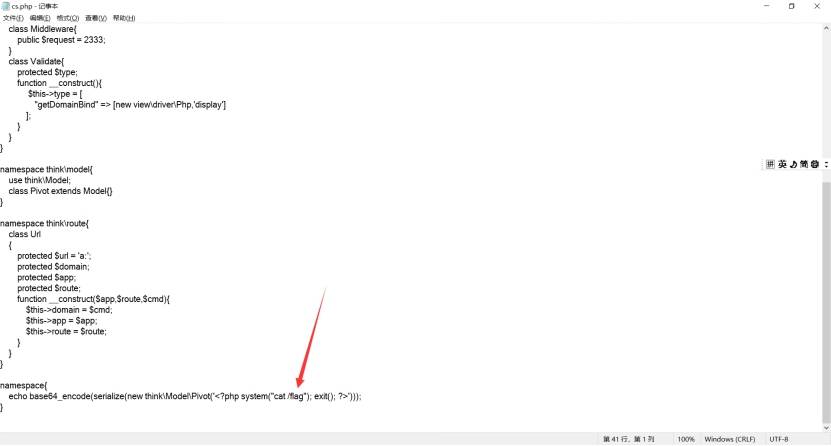
找到个eval链可用的
且存在直接的exp
本地服务器搭建扔进去生成序列化代码
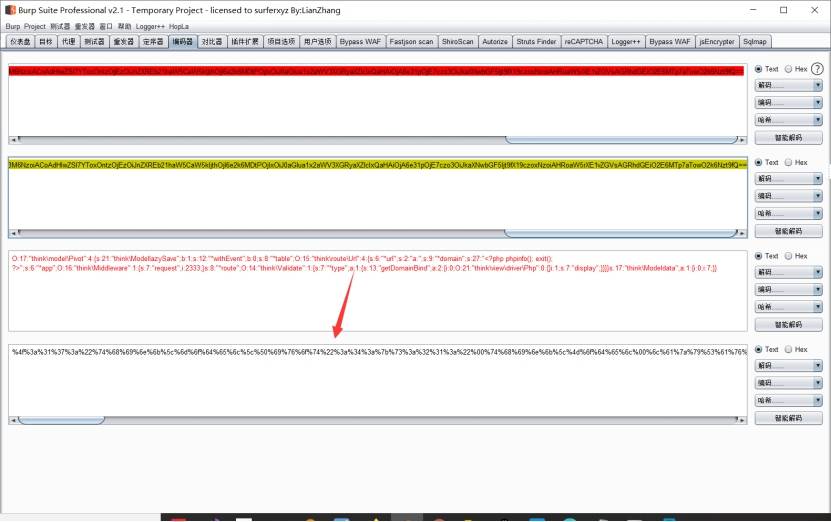
得到一个这玩意 base64编码的
解码后转url
把这串直接拿过去打
回显hacking
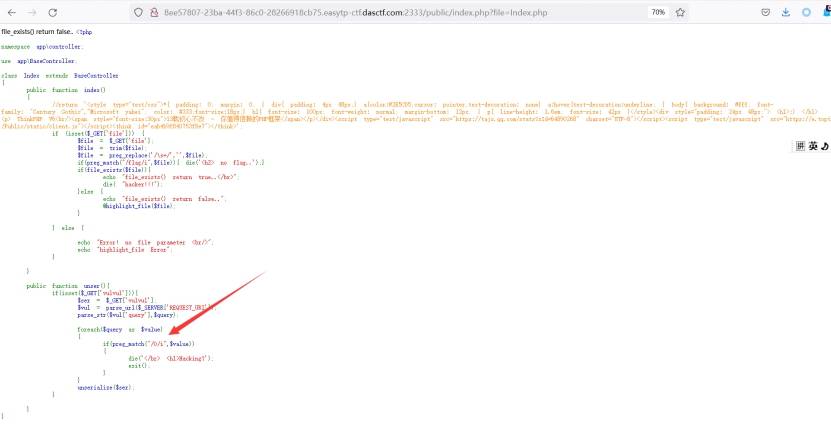
看了眼代码
是正则匹配的问题
绕呗还能咋搞
根据parse_url函数匹配的思路函数去绕
构造一个不合格的url即在public前加很多///符号
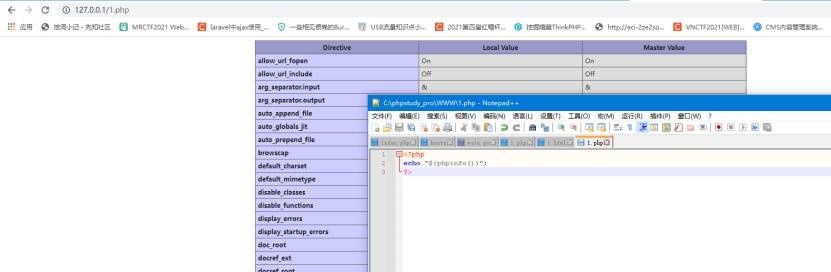
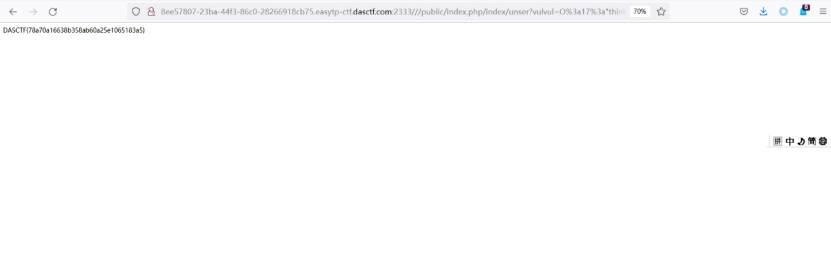
直接phpinfo
接下来就很常规了 把phpinfo的内容改成读取flag文件就好了
exp和之前的一样
生成解码编码打
收工跑路
PWN
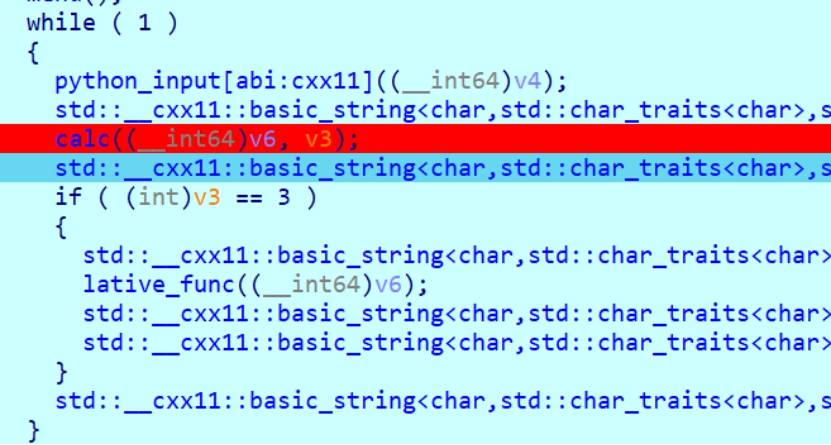
string_go By-f1ag
漏洞点在于lative_func()这,一开始分析v3是不受我们控制的,但发现动态调试后,如下,可以看见v3是有calc函数得来的。
因此我们先输入‘1+2‘即可进入lative_func()中
发现有输出函数,当v7=-1时即可输出栈上的内容。泄露出canary和libc
然后通过memcpy函数来覆盖返回地址执行rop
完整exp:
1 | PYTHON |
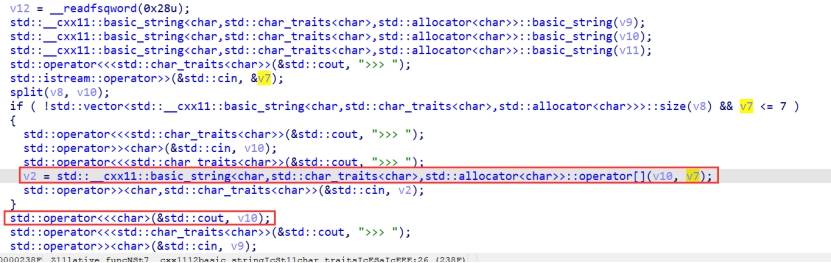
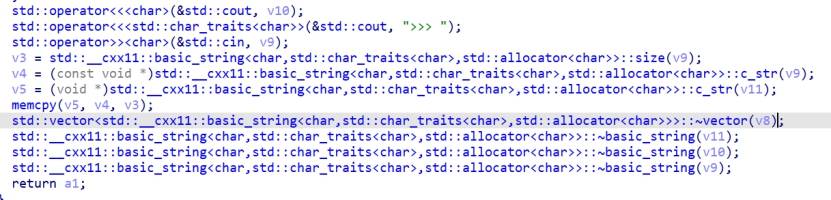
blind By-f1ag
发现alarm中有syscall,因此可以利用ret2syscall。利用csu那一大串pop可以对rdx置0,又因为没有libc,因此我们无法确定syscall具体在何处,因此我们需要爆破一个字节。
Exp:
1 | PYTHON |
RE
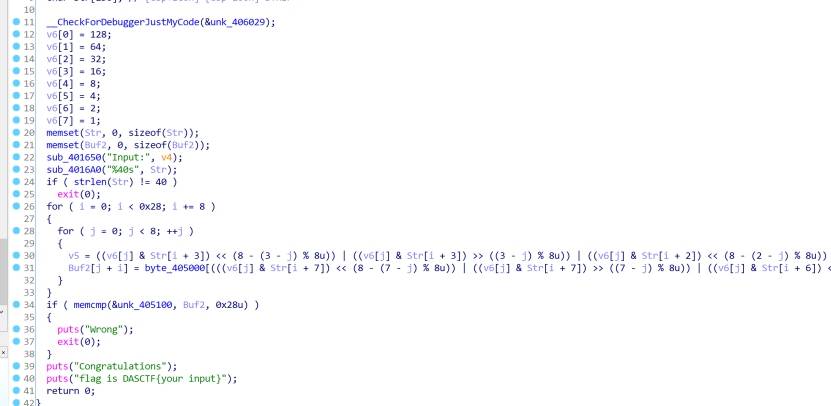
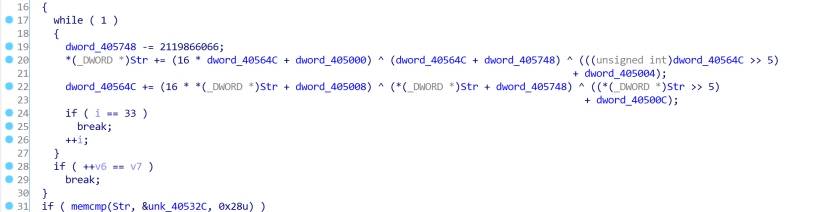
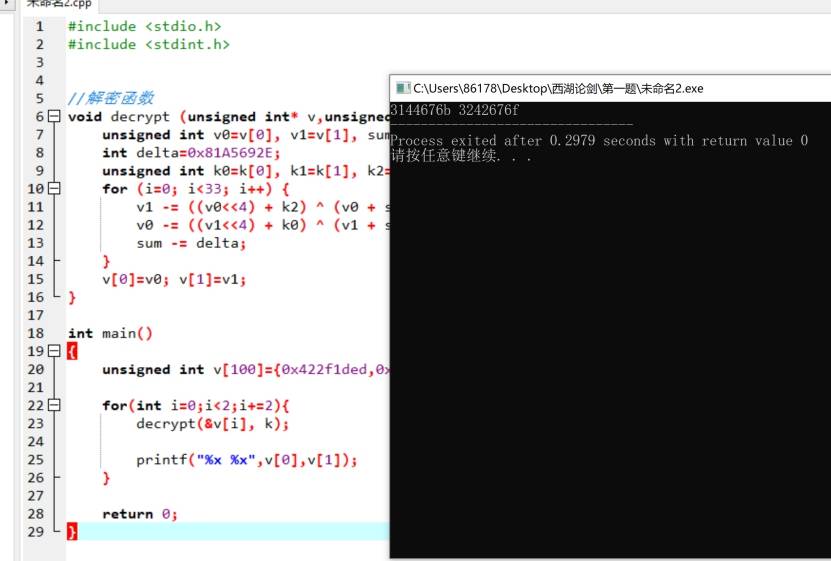
ROR By-yaoxixi
Flag40位,8个一组,一共5组
把8个字符串的相同位的bit取出,组成一个字节,与已知的明文串进行比较
两个for循环实现了这个操作,写脚本
1 | C |
得到要比较的字符串
把每一个字符串按照二进制展开,重新排列即可
把每一列连起来就是flag,依次拼接,手算得出flag
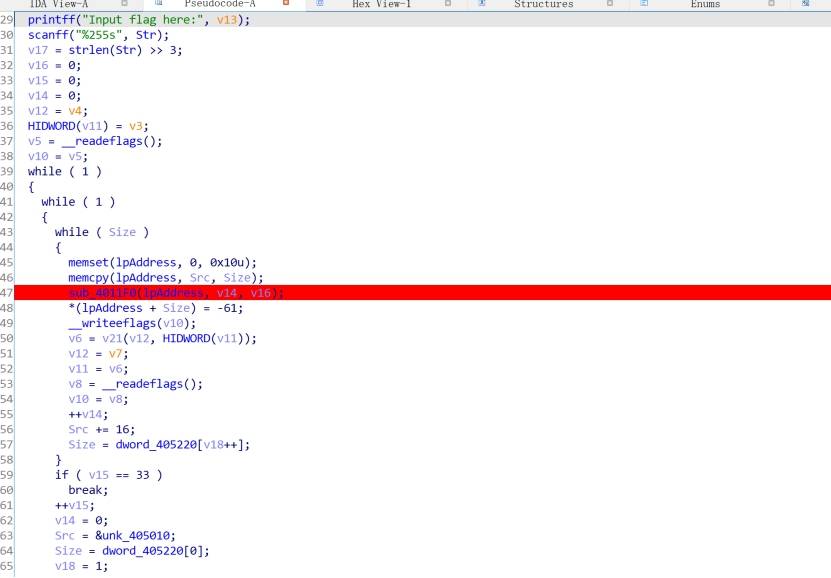
TacticalArmed By-yaoxixi
sub_4011F0函数把lpAddress的地址进行解密,最后调用了v21函数,用动态调试dump出程序,查看算法
观察dump出来的程序,再结合动态调试,可以发现这是一个魔改的base64
第一个改动的地方DELTA 改成0x81A5692E
第二个改动的地方解密循环增加了一次
第三个改动的地方每一次解密的sum值都不同,依次乘与12345
套脚本 拿到所有的数据
1 | C |
后面的数据类似,把拿到的数据逆序排列,即可拿到flag
Re4-虚假的粉丝 By-0xK4ws
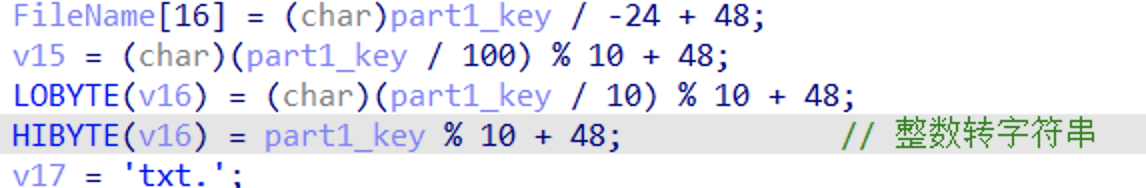
part1_key是数字 他在后面会进行整数转字符串的操作
然后在f文件夹里面的该数字对应的txt文件中 输入的第二个整形数据是该文件开始偏移所对应的字符位置 第三个要输入的整型数据是size
也就是从偏移对应的字符开始需要读取数据的大小
并且要保证该字符为U 从该字符开始向后偏移39个的字符是S
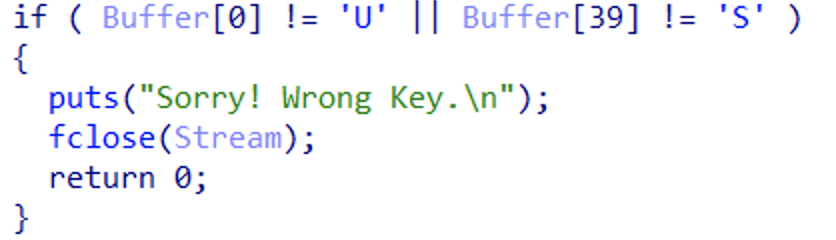
首先遍历f文件夹下的所有txt文件 找到既有字符U又有字符S的文件 发现只有一个4157
然后再进文件算U的偏移 为1118
Size是40
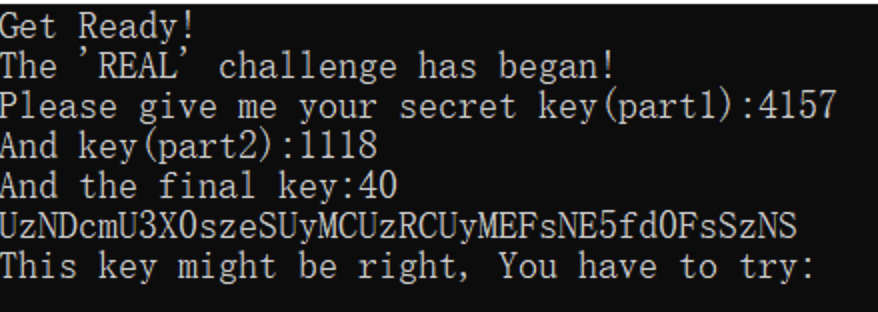
然后run程序依次输入上诉得到base64解码 得到S3Cre7_K3y%20%3D%20Al4N_wAlK3R Al4N_wAlK3R也就是第四次输入
然后输入完后等一首歌的时间 打开这个文件./f/ASCII-faded 5315.txt 就是flag











Q(@KJ)Y2G~V4.jpg)



